Understanding the risks and rewards of modernization is crucial to establishing a holistic approach to resilience.
Cyber State of the Union
Enterprises have become unprecedently reliant on complex and interdependent technology systems. While digital integration initiatives have undeniably improved the efficiency of service delivery through automation and the use of cloud infrastructure in a service-like fashion, they have also increased the number of attack vectors for fast-evolving cyber threats. With cybercrime growing 15 percent year over year, predicted to cost the global corporate system $10.5 trillion annually by 2025, the implications of mismanaged technology systems are critical.1 It is therefore essential to prioritize the security of interconnected systems today to mitigate the growing impact of cybersecurity concerns and protect enterprise value across industries.
Cybersecurity’s imperative role for an organization’s success is not a revelation; most organizations have implemented a threat management system that provides multi-layer protection across computers, networks, data, and applications. Since the development of firewalls in the late 1980s, and critical features such as spam filters, more recent techniques have emerged, including multi-factor authentication (MFA), network behavioral analysis (NBA), and real-time threat protection. Despite such advances, cyber attackers continue to innovate, discovering new ways to breach complex cybersecurity systems, thereby requiring more complex defense mechanisms to avert incidents that compromise both IT and business processes and result in lost revenue.
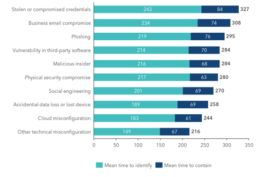
Due to the increasingly sophisticated and multi-pronged approach of modern-day cyberattacks, which include both technical and social means of deception, the time it takes for companies to even realize that an attack has taken place is generally several months on average (Exhibit 1). As a result, industries have started to broaden their focus beyond cybersecurity alone and are instead moving towards an emphasis on cyber resilience: an organization’s ability to not only prevent but also withstand and recover from cybersecurity incidents. Cyber resilience requires communication and coordinated responses surrounding cyber risk on an enterprise-wide scale. Without a holistic enterprise strategy, organizations will continue to fail when faced with cyber threats, risking significant economic loss and lasting reputational damage. However, cybersecurity departments too often continue to operate as a distinct body within their organization, thereby limiting the ability to detect and respond to threats systematically. According to a global 2022 Marsh and Microsoft study, surveying 650 industry leaders, only about 40% of organizations create comprehensive cyber risk and business continuity plans that engage their legal, finance, operations, or supply chain management functions.2 A shift towards a mindset were cyber is pervasive across all tech and business functions is paramount.
Exhibit 1. Average Time (Days) to Identify and Contain a Data Breach by Initial Attack Vector (Top 10)
The impact of cyber-attacks on day-to-day operations is expansive. Often, these attacks have led to severe supply chain disruptions, as demonstrated by the 2021 ransomware attack on The Colonial Pipeline’s systems, where all pipeline operations carrying gasoline and jet fuel were halted to contain the situation. This event marked one of the first high-profile breaches that originated from an employee’s stolen password, and not initiated through a direct attack on IT systems.3
Cybersecurity incidents are also not only a threat to corporations’ internal operations and bottom line; customer personally identifiable information and financial data is also at serious risk of exposure and misuse, in turn impacting customer perception and long-term brand loyalty. in 2019, Capital One experienced a cyberattack across roughly 100 million credit card applications, leaking over one million social security numbers and approximately 80,000 bank account numbers.4 This came shortly after an equally devastating incident in 2017, in which the personally identifiable information (PII) of over 145 million Americans, including addresses, birth dates, social security numbers, and other personal data – was hacked and harvested from Equifax, a consumer credit reporting agency.5
The increasing frequency and severity of these cyberattacks, involving both employee and customer personal data has increased since the onset of the COVID-19 pandemic, when the number of remote workers tripled.6 During the pandemic, approximately 80% of global organizations reported an increase in cyber threats, as well as increased downtime due to cyber-incidents during peak business hours, impacting employee productivity and profit potential. The pandemic has challenged companies across industries to rethink security practices and install next-gen technologies to protect employees and customers.
Work-from-home increasingly depends on personal devices, local networks, and cloud services, significantly expanding the possible avenues for cyberattacks.7 Companies that previously provided laptops only to field staff and external consultants now often face challenges due to the sudden COVID-19-initiated switch of many, if not most employees to the ‘home office’. Many employees access company networks using their own devices under bring-your-own-device (BYOD) policies. These devices are frequently not configured according to enterprise security policies and outdated or non-existent malware protection and security patches.
Modern Day Attack Patterns
Modern attackers have taken advantage of vulnerabilities exposed during the pandemic and the shift to a hybrid work environment.8 This validates that the ‘human factor’ remains the weakest link in cybersecurity. In 2022, 82% of data breaches involved human error, ranging from employees exposing information directly (e.g., by misconfiguring databases) to operational mistakes enabling cybercriminals to access the organization’s systems.9 In 2021, 46% of organizations had at least one employee download a malicious mobile application, and 97% of organizations faced mobile threats from several attack vectors.10 As the prevalence of reliance on mobile wallets and payment platforms increases, cybercriminals continue to discover novel ways to exploit this trend. In the face of these challenges, security teams must determine how to maintain an appropriate degree of access control without compromising user productivity and efficiency. Maturity models exist for measuring capabilities, digital transformation, supply chain, and data management; it is time for an analogous framework to help organizations measure and understand the maturity level of their cyber resilience posture and response strategy.
Exhibit 2. Internet Crimes Connected to the Greatest Financial Losses (2021, USD, M.)
At its core such a framework must assess the following:
1.How fast can an organization recover when experiencing a successful cyberattack
2.Which characteristics are indicative of high resiliency during potential attacks
3.What business areas an organization needs to prioritize as part of its cyber defense plans
4.What exposure results from legacy IT infrastructure,
as well as other known gaps within its enterprise tech stack
This multi-faceted approach allows firms to conduct sensitivity analyses and accurately prioritize structural changes within an organization, in turn facilitating the move towards a future state that reduces potential for human error and increases automation of security practices wherever possible. This includes source-level encryption of all personal data and sophisticated access control systems for sharing PII Meeting these table stakes for cyber resilience will be ever more critical for enterprise success and should, by default, include embracing enterprise CMDB and SBOM solutions.
The Premise of Cyber Resiliency
Effective cyber resiliency requires a holistic and adaptive approach capable of withstanding the evolving threats to core services and infrastructure. A program focused on continuously modernizing all systems, architecture, and processes is paramount for effectively mitigating threats. To build and maintain a position of cyber resilience, enterprise-wide digital dependencies and risks need to be reassessed, documented, and tracked. Security and network architecture built around a perimeter paradigm are no longer effective in the face of today’s ever-changing environmental demands. Instead of using legacy concepts to solve emerging problems, companies must rethink the current approach and re-architect their system landscapes, leveraging cutting-edge technologies and practices, including SD-WAN, DevSecOps, and SBOMs (see section 4).
Another novel yet critical component for building a truly resilient approach to cybersecurity is the embrace of zero trust architecture (ZTA) as part of an organization’s network design (Exhibit 3). Such an approach is built on the assumption that a network’s security is perpetually at risk and exposed to external and internal vulnerabilities, and therefore employs continuous threat mitigation.11 Zero trust-based systems never grant implicit trust to any resources or user accounts within the security perimeter of an enterprise; instead, zero trust-based systems emphasize protecting resources through specifying and enforcing identity-based control access policies (e.g., authentication, authorization) at the time and location of the access request by any given resource.
The adoption of ZTA principles is quickly becoming status quo, considering security threats, increasing data complexity, and expanding regulatory statutes, such as GDPR.
In particular, the growing business intelligence application universe has allowed data users to gain unrestricted access to data. We are seeing a shift in which enterprise business intelligence platforms, once centrally managed by IT departments, are now giving way to the use of self-service and data-service tools. Though many of the features imbedded in these tools lead to increased efficiency and output, there are serious governance implications that must be considered and can only truly be mitigated through the adoption of ZTA.
With the added emergence of more remote users and the widespread adoption of cloud-based infrastructure, adopting ZTA patterns has become paramount.12 Adoption of zero trust must consider three primary elements:
1.Software-defined perimeters
2.Micro-segmentation
3.Enhanced identity governance
The first, and perhaps most fundamental configuration method employs software-defined perimeters (SDPs) to mitigate internal and external network security attacks by restricting access to discrete enterprise infrastructure resources. In this implementation, each user must be verified before access is granted.
The second approach uses micro-segmentation, wherein the smallest possible perimeter is created around individual workflows or user groups within unique network segments. Micro-segmentation is a possible configuration for smaller, more static network environments, as it is suited for less complex infrastructure environments. However, micro-segmentation and SDPs rely on legacy IT boundaries. As systems become more complex, SDPs and micro-segmentation become progressively less effective.
The third configuration of zero trust relies on enhanced identity governance, wherein access is granted based on individual user privileges. Adopting identity governance allows for the most significant degree of security, as it does not rely on a physical or logical system perimeter. Instead, mature identity governance approaches rely on continuous (re)enforcement of user privilege (e.g., by employing multi-factor authentication, behavioral analysis, and metadata evaluation). Indeed, due to rapidly growing technological complexity, identity placement is the most crucial factor in prioritizing security and will enable networks to grow without the fear of them becoming “too large to secure.”
Exhibit 3. Comparison of perimeter-based and zero trust architecture (ZTA) paradigms
Exhibit 4. Traditional vs. SD-WAN
Emerging Implication and Novel Threats
Cyber resiliency entails effectively responding to and preparing for attacks in real-time and enabling organizations to effectively anticipate future threats. Understanding emerging risks and countering modern cyberattacks is key to effectively ensuring an organization’s readiness to withstand and recover from cyber-related incidents.
Attacks on container and serverless environments are two examples of threats to recent technologies. Due to the novelty and quickly evolving standards surrounding containerized applications, vulnerabilities resulting from misconfigured environments occur frequently. In the absence of an overarching defense strategy, this weakness can easily be exploited by malicious actors.
While it is convenient for developers to leverage fully outsourced environments and exclusively focus on high-level functionality, this approach also results in a new level of risk exposure, as the entity becomes entirely reliant on external services provided by third parties. Similarly, serverless computing, where micro servers are directly deployed on infrastructure wholly managed by a third party, constitutes a rapidly growing space with a new set of core vulnerabilities that may be easily overlooked. In a cyberattack, an organization’s control to mitigate is nominal. Tooling and best practice recommendations for defending against attacks within container environments and for server-less architecture paradigms are still nascent; organizations therefore need to take this into consideration when devising their technology selections and strategic planning.
Another example of a risk that has arisen in the broader adoption of new technology is the uncontrolled use of cloud capacity and personal computing devices in a shadow IT fashion. Shadow IT refers to using IT systems, devices, software, applications, or services without explicit approval from an IT department. While this has always posed a risk to organizations, this risk has grown as work outside of traditional workplaces has become more widespread. Whether it is to avoid bottlenecks due to change in control processes or for the sake of simplifying daily tasks, it is not uncommon for employees’ personal payment methods to be used for cloud spending. Non-company-managed cloud accounts result in significant security exposure, as enterprise security teams are unaware that they exist in the first place and cannot account for them in their defense plans. Companies should therefore enable the streamlined deployment of cloud capacity in a managed, secure, authorized manner – whether this means offering more secure, but comparable alternatives, or bolstering trust in IT advisors. To guarantee resilience and security, organizations must ensure that IT departments know where all internal systems and data are hosted.
Investing in Cyber Resilience
Often the most difficult question posed to IT cybersecurity leaders, especially in the context of large-scale multinational enterprises operating multi-cloud environments, is where their organization should place its investment dollars to prepare against cybersecurity threats most adequately. In focusing on tactical mitigation efforts such as AI-aided threat monitoring, companies often do not prioritize bolstering their fundamental IT capabilities until there is a major upset, as any returns on investment (ROI) are difficult to estimate. However, considering the rapid progress of cloud expansion, combined with the latest geopolitical shifts and trends towards supply chain decentralization, attack surfaces will continue to increase, and the impact of cyber-attacks is also ever-increasing. Cybersecurity investments today will undoubtedly reap benefits in the long term, and there are several no-regret actions that can be taken today to embark on a journey towards becoming cyber resilient.
The Australian Cyber Security Centre (ACSC) publishes a prioritized list of mitigation activities to help cybersecurity officials navigate and effectively mitigate the impact of cyber threats. The list describes strategies to address specific incidents caused by, for example, targeted intrusions, ransomware attacks, malicious insiders, or compromised emails. For each of these causes, the ACSC outlines detailed mitigation strategies, expected upfront costs, ongoing maintenance costs and potential areas for user resistance.
The primary effort, however, must be to identify existing assets and conduct a thorough risk assessment to determine the level of protection required against potential threats. Additionally, motivators such as cyber-attacks, penetration tests, compliance requirements, or data breach reporting must be identified to initiate the transformation process. For example, mitigation strategies for reducing the number of cyber-related security incidents should include a core set of essential controls, including administrative privileges, patching operating systems, implementing multifactor authentication, strict IAM policies, including least-privileged-access, and network segmentation.
Similarly, the Center for Internet Security (CIS) publishes a set of actionable security controls developed from key security concepts.13 These controls, initially published through a partnership between the U.S. government and several private sector security research organizations, are prioritized in order of criticality, making it easy for organizations to understand the most crucial implementations they should focus on first.14 Such hierarchical lists of actions are particularly helpful for organizations looking to embark on their cyber resilience journey, as they provide an easy-to-follow roadmap, helping IT leaders to understand where investments will be most impactful. For example, CIS lists amongst the top security controls the creation of an “inventory of authorized and unauthorized devices and software,” This objectifies the process of evaluating technologies and devices, allowing firms to re-allocate resources to more complex resilience design areas.
Making the Change to ZTA
For organizations looking to strengthen their security posture, critical consideration must be given to the adoption of ZTA principles. NIST recently published a draft of the SP 1800-35, outlining implementation recommendations for firms looking to embrace ZTA. The proposed reference architecture centers around policy enforcement points, controlling resource access based on a set of centrally administered, user-specific rules. Enterprises should design a gradual roll-out and risk-based approach. Setting and prioritization of sequential milestones across the enterprise environment should also be utilized.
Exhibit 5. ZTA High-Level Architecture (NIST)
In Closing..
Traditional cyber security controls are proving to be insufficient against the ever-changing virtual landscape. Bolstering an organization’s ability to prevent, withstand, and recover from cyber security incidents is becoming pivotal to its commercial success.
At its core, cyber resilience is about proactivity; the most effective measure an organization can take is to continue to anticipate threats that are likely to evolve with the growing complexity of their systems. Cyber-related investments often do not show an immediate ROI on paper and are therefore difficult to justify from a first-order business case perspective. Nonetheless, these investments are crucial in the long term and should be considered non-negotiable. Organizations that take a proactive, innovation-driven, and adaptive approach to cyber resilience across the enterprise will set themselves apart by protecting their assets, reputation, and customers alike. Instead of responding to incidents reactively, an embrace of modern capabilities, such as SD-WAN, ZTA, and SBOM will pay lasting dividends.
- Freeze, Di. “Cybercrime to Cost the World $10.5 Trillion Annually by 2025.” Cybercrime Magazine.
- The State of Cyber Resilience Report
- Turton, William. “Pipeline Cyber Attack: Hackers Used Compromised Password.” Bloomberg.
- “2019 Capital One Cyber Incident: What Happened.” Capital One.
- “Chinese Hackers Charged in Equifax Breach.” FBI..
- “Bureau, US Census. “The Number of People Primarily Working from Home Tripled” Census.gov.
- “Shaping the Future of Cybersecurity and Digital Trust Cybersecurity”, WeForum.
- “The State of Cyber Resilience.” Marsh.
- “2022 Data Breach Investigations Report.” Verizon Business
- “Why We Need to Move from Cyber Security to Cyber Resilience.” World Economic Forum.
- “What Is Zero Trust?” IBM.
- Software Defined Perimeter (SDP) and Zero Trust – Waverley Labs.
- Prokopets, Marie. “CIS Controls V8 vs. CIS Top 20 Critical Security Controls.” Nira.
- Controls Practical Guidance for Web V4 – Center for Internet Security.